Locks and Security News: your weekly locks and security industry newsletter
24th July 2024 Issue no. 715
Your industry news - first
We strongly recommend viewing Locks and Security News full size in your web browser. Click our masthead above to visit our website version.
The What, When, Where, Who, How and Why behind security incidents
 Security people can be infuriating. All too often security incidents are confused in a fog of acronyms, data, and analysis. The industry, as a whole, has failed to make information presentation humanly readable and visual.
Security people can be infuriating. All too often security incidents are confused in a fog of acronyms, data, and analysis. The industry, as a whole, has failed to make information presentation humanly readable and visual.
At SecurityHQ we have adopted some simple methods of investigation used by police forces and philosophers for thousands of years.
Picture the scene of a crime; and enter our hero... the police investigator. As he scans the scene for evidence, he tries to build a picture of the events that led to this crime. There are only 6 questions in his mind... What, When, Where, Who, Why and How?
And so, to solve a problem, either in the physical world, or your cyber environment, these elements are the factors you must question and decipher to solve a problem or collect the right information.
We call this method "5W+H".
This is not something new, we can trace the origins of 5W+H back to ancient Greece and to Aristotle in his 'Nicomachean Ethics' who used this framework to decide and evaluate the morality of actions in reference to a given situation by determining what should be done or what was done, who it was done by, how it was done, where, and why.
But why hasn't the Cyber Security Community adopted this approach?
We have no logical answer to this, other than the observation that all too often there is a tendency for analytics to create confusion with a jumble of unstructured analysis.
We are changing the game. Structured investigation, simplicity and human readable analysis is our objective.
Since Aristotle's earliest account, writers, philosophers, scientists, mathematicians and more have based their work surrounding these six questions.
"I keep six honest serving-men?(They taught me all I knew);?Their names are What and Why and When?And How and Where and Who"
- Rudyard Kipling, Just So Stories, 'The Elephants Child' (1902)
Let us now show how this method can be applied to our security platform.
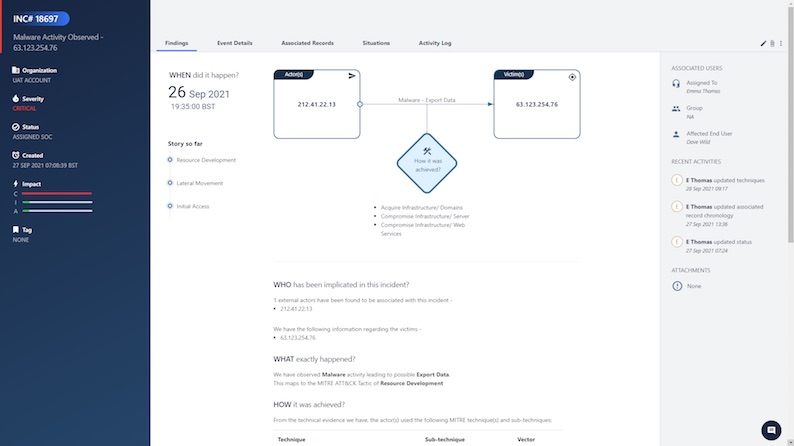
5W,1H Method - What, When, Where, Who, How and Why of Incident Record
Added to the Incident record are subsections for 'What, When, Where, Who, How and Why' to provide clear guidance of each incident.
What - The 'What' tab shows exactly what happened, what was the intent of the actor, and what was the impact of the incident. Existing fields such as the Incident Area (Action) and the Confidentiality Integrity & Availability (CIA) impact will be moved to this category to keep all information together and easily accessible.
When - The 'When' tab shows the date and time of the occurrence.
Where - The 'Where' tab shows the geo-locations of the external entities, and victim geolocations/network locations. The previous 'Where' feature had limitations in that it was not showing exactly which part of the network the internal hosts belonged/belongs to. Now, under this subsection we go beyond locations, to provide insight into where exactly in the internal network a particular host lies.
Who - The 'Who' tab highlights those associated with the incident, what types of identities (actors and assets) and who has been identified as the victim/victims? The following points are highlighted in this section.
Actor/ Actors
Victim/Victims
- Actor: External/Internal
- Asset Type
- IP Address
- Asset Subtype
- Domain
- Hostname/ IP Address
- Username
- Username
- Intelligence: Reputation
- Target Port
- Intelligence: Association
How - The 'How' tab shows how the activity was carried out, what attack vectors and techniques/sub-techniques were used, and what was the modus operandi.
Why - The 'Why' tab shows why the incident was possible in the customers' network in the first place and what the risk level and control areas were, to pinpoint where exactly security controls need to be enhanced.
Important Details
- This information will be used as the foundation for the situation-based analytics.
- The enhancements will be provided to all interfaces and subsequently, on mobile apps.
- The new incident record structure will be supported by all SecurityHQ interfaces, including the APIs that are used behind the scenes.
New Interactive Layout
The overall layout has been changed so that it is clean and user friendly, that technical information is presented in plain English for easier consumption, and smart interactive graphics are used for instant visibility.
Instead of using the previous top-level header to show important info, we now use the entire space available, so that the left bar shows the important details including the CIA impact, and the right side now shows multiple tabs in which content is divided.
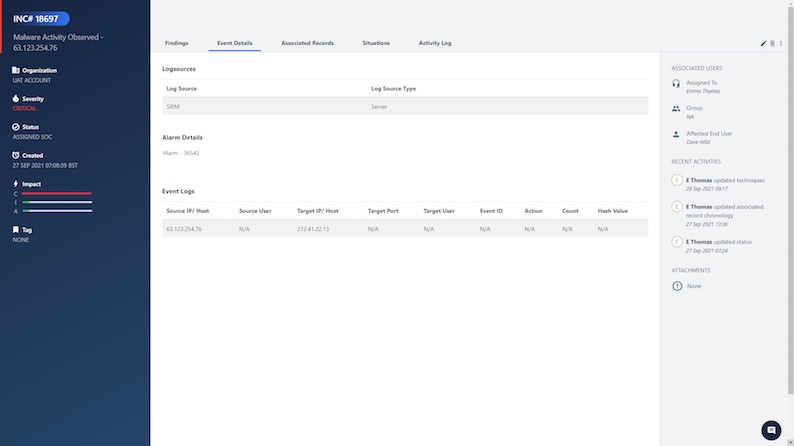
Event Detail Tab
The Event Detail Tab shows information about the log sources, the alarm and the event logs as associated with Security Information & Events Management (SIEM) offense.
 Associated Records Tab
Associated Records Tab
This is useful to help capture any events/episodes associated with the incident, both past and future. Say a particular incident mentions data exfiltration and data collection, but it had an initial access episode a few months back and the malware got executed and evaded the network defences, those episodes can now be captured as associated records. The associated records will help the platform present a chronological story for the incident.
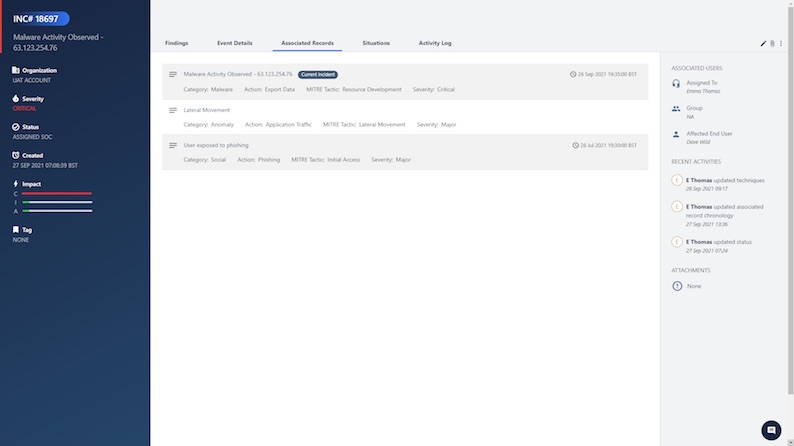 There is also two-way versatility here with the 'Situations' tab. This tab will show a list of situations that this incident is a part of, so you can come to an incident via the situations, and you can go back to the situations through the incident record. The same view is presented to SecurityHQ customers.
There is also two-way versatility here with the 'Situations' tab. This tab will show a list of situations that this incident is a part of, so you can come to an incident via the situations, and you can go back to the situations through the incident record. The same view is presented to SecurityHQ customers.
This is a significant change in terms of presentation, as well as the way the data is structured. Instead of all this technical information becoming a part of large text block, separate sections and sub sections are provided to capture information.
Our award-winning Incident Management Platform covers all the services that SecurityHQ delivers. Regardless of whether it is MDR, EDR, Vulnerability Management, and so on, customers can go to one place to see their security environment instantly.
About SecurityHQ
SecurityHQ prides itself on its global reputation as an advanced Managed Security Service Provider, delivering superior engineering-led solutions to clients around the world. By combining dedicated security experts, cutting-edge technology and processes, clients receive an enterprise grade experience that ensures that all IT virtual assets, cloud, and traditional infrastructures, are protected.
Author: Eleanor Barlow , Content Manager, SecurityHQ
Facebook: www.facebook.com
Twitter: https://twitter.com/security_hq
LinkedIn: www.linkedin.com
3rd November 2021








