Locks and Security News: your weekly locks and security industry newsletter
25th June 2025 Issue no. 759
Your industry news - first
We strongly recommend viewing Locks and Security News full size in your web browser. Click our masthead above to visit our website version.
Malicious ISATAP Tunneling unearthed on Windows Servers
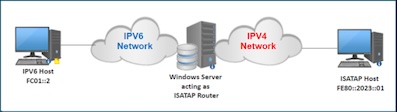 ISATAP is an IPv6 transition mechanism that allows IPv6-in-IPv4 tunnels to be created automatically within a site.
ISATAP is an IPv6 transition mechanism that allows IPv6-in-IPv4 tunnels to be created automatically within a site.
Each host queries an ISATAP router within the site to obtain the address and routing information. Packets sent to the IPv6 Internet are routed via the ISATAP router, and packets destined for other hosts within the same site are tunneled directly to the destination.’*
IP stands for Internet Protocol. IPv4 stands for Internet Protocol version 4 and is, despite the name, the first version of IP to be used. IPs are designed to combine multiple numbers and periods, which form an identity for the user to connect to the internet, and from there access and use data. IPv6 is the most recent version, formed with IPv4 could no longer withstand the capabilities needed with regards to the increased volume of internet users.
How ISATAP is Configured-on Windows Servers
A Windows Server can function as an ISATAP router when it has one interface connected to an IPv6 network and another to an IPv4 network. By enabling the 'IPEnableRouter' registry setting and configuring the interfaces, the Windows Server can act as an ISATAP router. Once properly configured, machines from the IPv6 network can communicate with machines in the IPv4 network seamlessly. Almost all versions of Windows Operating System support “ISATAP” protocol.
How ISATAP is Leveraged by Cyber Threats
The ISATAP protocol is originally designed for intra-network communication. During a security investigation conducted by the SecurityHQ Digital Forensics and Incident Response (DFIR) team, it was seen being exploited by cyber actors. The team discovered that an external actor had maliciously configured from an internal IPv6 network directly to a 'Command-and-Control' IP, establishing a network bridge between the internal network and the attacker's network. This unauthorized connection bypassed existing network security measures, enabling the attacker to gain control over the network without triggering detection by any security controls. While this tactic is not currently associated with any specific cyberattack or APT group, it poses a potential threat that may be leveraged in the future.
How to Detect Malicious ISATAP Tunneling
- Monitor for communication towards suspicious IPs and ports within your network.
- Check for Windows System event IDs 4100 (ISATAP address configuration) and 4200 (ISATAP Tunnel brought UP) in the event viewer logs.
- Review changes made to the 'IPEnableRouter' registry setting on Windows Servers, as unexpected modifications may indicate malicious activity.
- Examine network DNS server logs for events related to the activation or configuration of the 'ISATAP' protocol.
Mitigation Steps
- Check for any active ISATAP tunnel, use the command or PowerShell:
netsh interface ipv6 isatap show state
To disable the tunnel, user below command –
netsh interface ipv6 isatap set state disabled
- If you are not actively using the ISATAP protocol, consider disabling it on all Windows servers by applying a Group Policy Object (GPO).
In the event of detecting an active ISATAP tunnel or any suspicious activity, immediately contact your Incident Response team, to investigate the initial vector and take necessary actions to contain the potential attack in progress, or contact SecurityHQ to speak with an expert, here.
About SecurityHQ
SecurityHQ is a Global MSSP, that detects, and responds to threats, instantly. As your security partner, we alert and act on threats for you. Gain access to an army of analysts that work with you, as an extension of your team, 24/7, 365 days a year. Receive tailored advice and full visibility to ensure peace of mind, with our Global Security Operation Centres, and utilize our award-winning security solutions, knowledge, people, and process capabilities, to accelerate business and reduce risk and overall security costs.
* IEEE, ‘The implementation of ISATAP router’
Website: securityhq.com
31st January 2024








